Securing a Web Experience with SSL
Secure Sockets Layer (SSL) is the standard security technology for establishing an encrypted link between a web server and a browser. This link ensures that all data passed between the web server and browsers remain private and integral. SSL is an industry standard and is used by millions of websites in the protection of their online transactions with their customers.
Notes on using SSL with Brightcove Engage
- Publishers are responsible for the SSL certificate
- Self-signed certificates are not supported
- The private key cannot be encrypted with a password
- The maximum SSL certificate key length supported by Brightcove Engage is 2048 bits
- Brightcove requires the certificate to be in PEM format
- Brightcove recommends that SSL certificates used in Brightcove Engage not be used anywhere else
- Publishers must use a custom domain name
Configuring a Web Experience for SSL
These steps assume you have purchased an SSL certificate. Your Web Experience must also be configured to use a custom domain. For information on configuring a Web Experience to use a custom domain, see Configuring Custom Domains and SSL.
Upload the SSL certificate
- Open Brightcove Engage.
- Open the Projects page and click the Settings link at the top of the page.
- In the left navigation, click the Custom Domains & SSL link.
- Edit the custom domain that SSL will be enabled for.
- Check Use SSL.
- Paste in your Server Certificate. Remove any blank lines at the beginning or end of the key. Brightcove requires the certificate to be in PEM format.

- Paste in your Server Private Key. Remove any blank lines at the beginning or end of the key. Brightcove requires the certificate to be in PEM format.

- Paste in your Chain of CA Certificates. If your certificate was signed by a root CA, then only the root certificate CA needs to be pasted in. This should not include your own certificate. Remove any blank lines at the beginning or end of the key. Brightcove requires the certificate to be in PEM format.
- Click Save. The site details will be displayed.
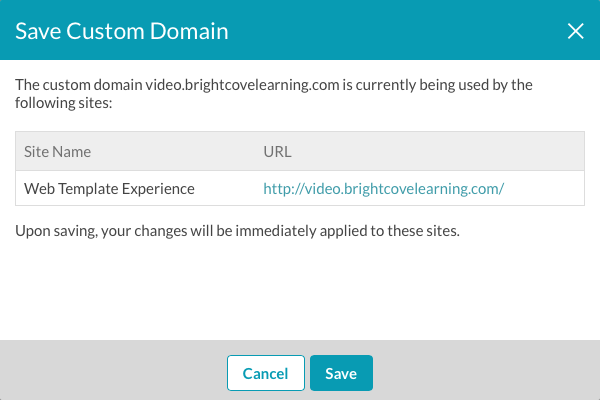
- Click Save. The certificate will be validated and if there are errors, they will be displayed.
The SSL status will display Updating Configuration while the SSL information is being updated and propagated. Click Refresh List to update the SSL status.
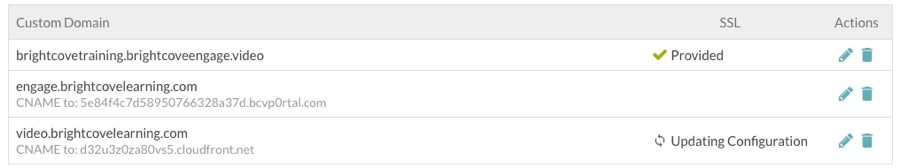
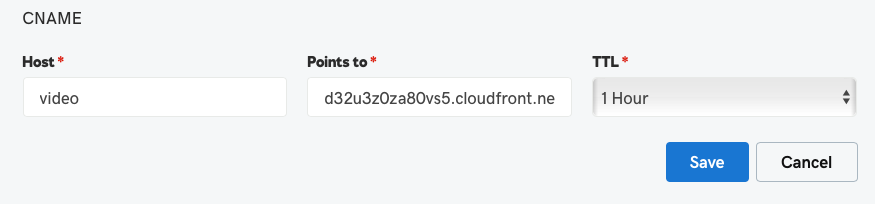
Configure the CNAME record
Once SSL has been configured, the SSL status will be Enabled. The CNAME information will be updated with a CloudFront URL. The CloudFront URL will not change unless the domain is deleted.
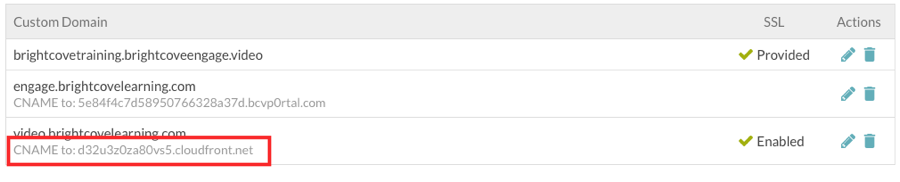
Note that browsing directly to a CloudFront URL will return a "page not found" error (404). A curl command can be used to verify the domain configuration. For this example:
curl -H "Host: video.brightcovelearning.com" https://d32u3z0za80vs5.cloudfront.net
The curl statement should return the contents of the site home page.
The CNAME record for your custom domain should redirect to the CloudFront URL displayed on the Custom Domains and SSL page.
Updating/Replacing SSL certificates
If an SSL certificate needs to be updated or replaced, for example, the SSL certificate may be set to expire, follow these steps to replace an existing SSL certificate.
- Open Brightcove Engage.
- Open the Projects page and click the Settings link at the top of the page.
- In the left navigation, click the Custom Domains & SSL link.
- Edit the custom domain that SSL will be enabled for.
- Click Upload new certificate.
- Paste in the new Server Certificate, Server Private Key and Chain of CA Certificates. Remove any blank lines at the beginning or end of the keys.
- Click Save.
If there are any errors with the updated keys, the old values will be retained.
Sample keys
Below are examples of some sample certificates/keys.
Sample server certificate
-----BEGIN CERTIFICATE----- MIIDXTCCAkWgAwIBAgIJAJC1HiIAZAiIMA0GCSqGSIb3DQEBBQUAMEUxCzAJBgNV BAYTAkFVMRMwEQYDVQQIDApTb21lLVN0YXRlMSEwHwYDVQQKDBhJbnRlcm5ldCBX aWRnaXRzIFB0eSBMdGQwHhcNMTExMjMxMDg1OTQ0WhcNMTIxMjMwMDg1OTQ0WjBFA .... MANY LINES LIKE THIS .... .... MANY LINES LIKE THIS .... JjyzfN746vaInA1KxYEeI1Rx5KXY8zIdj6a7hhphpj2E04LDdw7r495dv3UgEgpRC3Fayua4DRHyZOLmlvQ6tIChY0ClXXuefbmVSDeUHwc8YufRAERp2GfQnL2JlPULB7xxt8BVc69rLeHV15A0qyx77CLSj3tCx2IUXVqRs5mlSbq094NBxsauYcm0A6Jq vA== -----END CERTIFICATE-----
Sample server private key
-----BEGIN RSA PRIVATE KEY----- MIIDXTCCAkWgAwIBAgIJAJC1HiIAZAiIMA0GCSqGSIb3DQEBBQUAMEUxCzAJBgNV BAYTAkFVMRMwEQYDVQQIDApTb21lLVN0YXRlMSEwHwYDVQQKDBhJbnRlcm5ldCBX aWRnaXRzIFB0eSBMdGQwHhcNMTExMjMxMDg1OTQ0WhcNMTIxMjMwMDg1OTQ0WjBF .... MANY LINES LIKE THIS .... .... MANY LINES LIKE THIS .... JjyzfN746vaInA1KxYEeI1Rx5KXY8zIdj6a7hhphpj2E04LDdw7r495dv3UgEgpRC3Fayua4DRHyZOLmlvQ6tIChY0ClXXuefbmVSDeUHwc8YufRAERp2GfQnL2JlPULB7xxt8BVc69rLeHV15A0qyx77CLSj3tCx2IUXVqRs5mlSbq094NBxsauYcm0A6Jq vA= -----END RSA PRIVATE KEY-----
Sample chain of CA certificates
-----BEGIN CERTIFICATE----- MIIDXTCCAkWgAwIBAgIJAJC1HiIAZAiIMA0GCSqGSIb3DQEBBQUAMEUxCzAJBgNV BAYTAkFVMRMwEQYDVQQIDApTb21lLVN0YXRlMSEwHwYDVQQKDBhJbnRlcm5ldCBX aWRnaXRzIFB0eSBMdGQwHhcNMTExMjMxMDg1OTQ0WhcNMTIxMjMwMDg1OTQ0WjBF .... MANY LINES LIKE THIS .... .... MANY LINES LIKE THIS .... JjyzfN746vaInA1KxYEeI1Rx5KXY8zIdj6a7hhphpj2E04LDdw7r495dv3UgEgpRC3Fayua4DRHyZOLmlvQ6tIChY0ClXXuefbmVSDeUHwc8YufRAERp2GfQnL2JlPULB7xxt8BVc69rLeHV15A0qyx77CLSj3tCx2IUXVqRs5mlSbq094NBxsauYcm0A6Jq vA -----END CERTIFICATE----- -----BEGIN CERTIFICATE----- MIIDXTCCAkWgAwIBAgIJAJC1HiIAZAiIMA0GCSqGSIb3DQEBBQUAMEUxCzAJBgNV BAYTAkFVMRMwEQYDVQQIDApTb21lLVN0YXRlMSEwHwYDVQQKDBhJbnRlcm5ldCBX aWRnaXRzIFB0eSBMdGQwHhcNMTExMjMxMDg1OTQ0WhcNMTIxMjMwMDg1OTQ0WjBF .... MANY LINES LIKE THIS .... .... MANY LINES LIKE THIS .... JjyzfN746vaInA1KxYEeI1Rx5KXY8zIdj6a7hhphpj2E04LDdw7r495dv3UgEgpRC3Fayua4DRHyZOLmlvQ6tIChY0ClXXuefbmVSDeUHwc8YufRAERp2GfQnL2JlPULB7xxt8BVc69rLeHV15A0qyx77CLSj3tCx2IUXVqRs5mlSbq094NBxsauYcm0A6Jq vA== vA== -----END CERTIFICATE----- -----BEGIN CERTIFICATE----- MIIDXTCCAkWgAwIBAgIJAJC1HiIAZAiIMA0GCSqGSIb3DQEBBQUAMEUxCzAJBgNV BAYTAkFVMRMwEQYDVQQIDApTb21lLVN0YXRlMSEwHwYDVQQKDBhJbnRlcm5ldCBX aWRnaXRzIFB0eSBMdGQwHhcNMTExMjMxMDg1OTQ0WhcNMTIxMjMwMDg1OTQ0WjBF .... MANY LINES LIKE THIS .... .... MANY LINES LIKE THIS .... JjyzfN746vaInA1KxYEeI1Rx5KXY8zIdj6a7hhphpj2E04LDdw7r495dv3UgEgpRC3Fayua4DRHyZOLmlvQ6tIChY0ClXXuefbmVSDeUHwc8YufRAERp2GfQnL2JlPULB7xxt8BVc69rLeHV15A0qyx77CLSj3tCx2IUXVqRs5mlSbq094NBxsauYcm0A6Jq vA== vA== -----END CERTIFICATE-----
FAQs
- Can a Brightcove Engage Web Experience with a custom domain and SSL be only accessible via HTTPS? Yes, in fact this is the only way we allow the site to be accessed. If you try to access a site on the HTTP link, you will automatically be redirected to the HTTPS site. This is done by forcing HTTPS redirects in CloudFront.

