Securing Experiences Using Okta
When an experience is secured using SSO, users will be required to authenticate before they can access a Web or Mobile App Experience.
The steps in this topic assumed you have signed up for an Okta trial account, signed into your account and can access the Okta Dashboard page.
Creating an application
Start by creating an application.
- Log in to your Okta trial account.
- Click Applications in the top header.
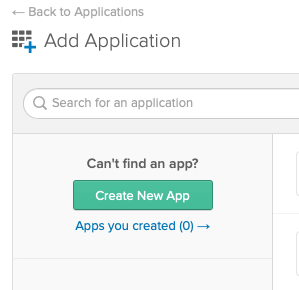
- Click Add Application.
- On the Add Application page, click Create New App.
- Select a Platform of Web and a Sign on method of SAML 2.0.
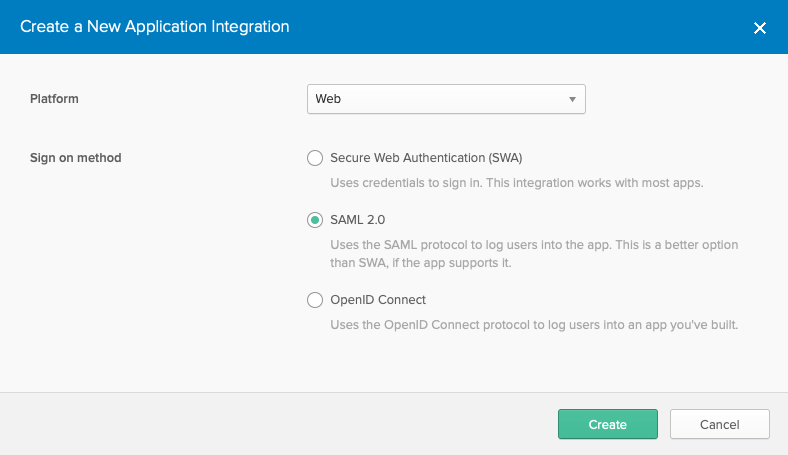
- Click Create.
- Enter an App name.
- (Optional) Browse and select and App logo.
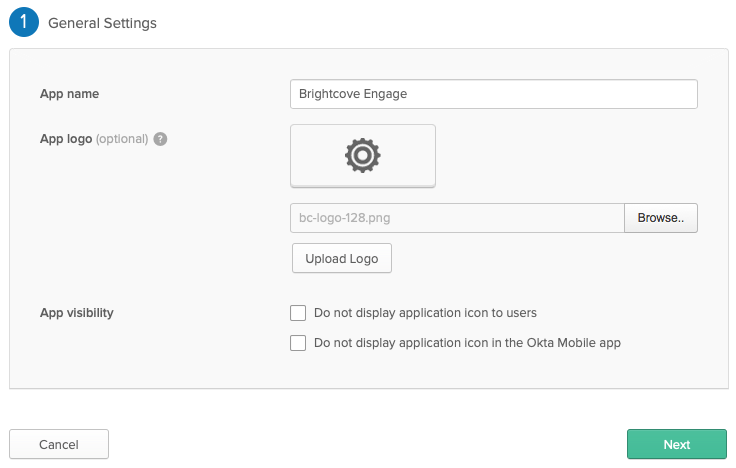
- Click Next.
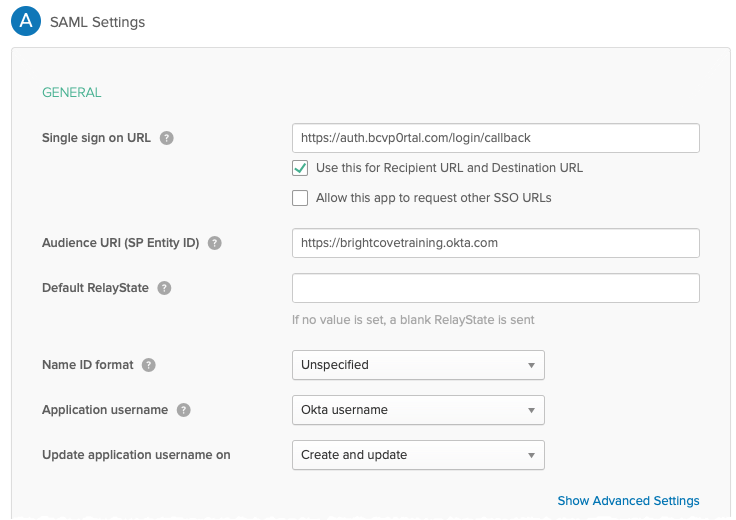
- Set the Single sign on URL to https://auth.bcvp0rtal.com/login/callback.
- For the Audience URI (SP Entity ID) enter the Okta URL for your Okta homepage. This will be listed on the new account email you received from Okta when your trial account was created.
- In the ATTRIBUTES STATEMENTS section, the following attributes should be created:
Name Value firstName user.firstName lastName user.lastName email user.email 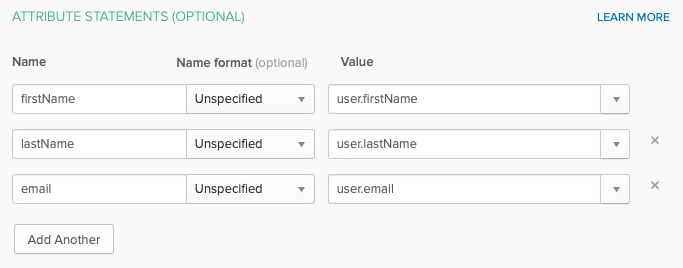
Mapping the application attributes will cause the following to happen in Brightcove Engage Experiences:
- For Mobile App Experiences, the user's name and email address will appear on the Profile page
- For all experiences, the user's email address will appear as part of video analytics
- Click the <> Preview the SAML Assertion button. Valid XML should be displayed in a new browser tab. If there are any errors, a message will be displayed.
- Click Next.
- Select an option for Are you a customer or partner? and then click Finish.
- Confirm that the application was created and the Settings page appears.
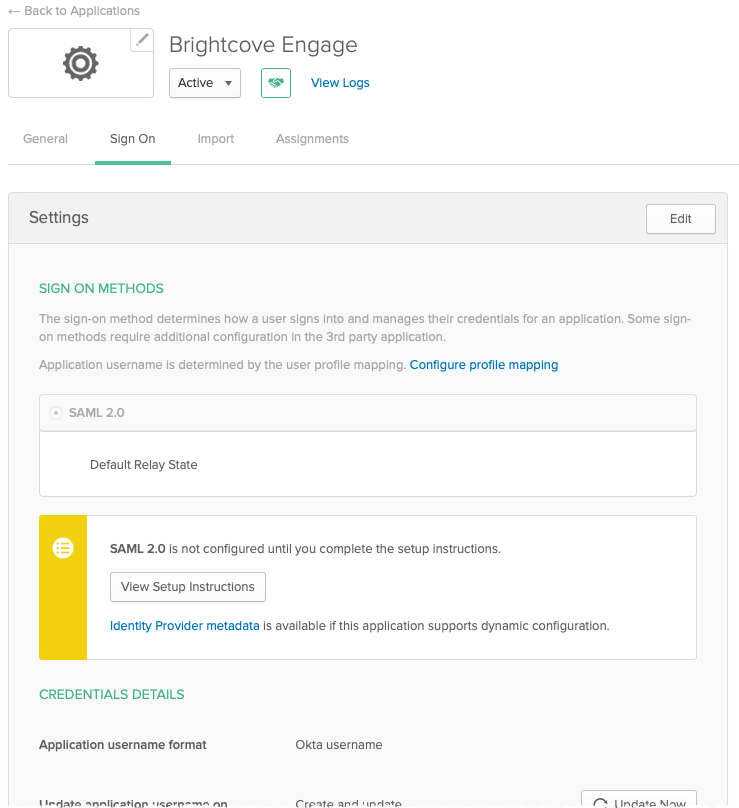
- Locate where it says SAML 2.0 is not configured until you complete the setup instructions. Click View Setup Instructions.
The How to Configure SAML 2.0 instructions will open in a new browser tab. This information will be needed when creating an Access Control Profile in Brightcove Engage.
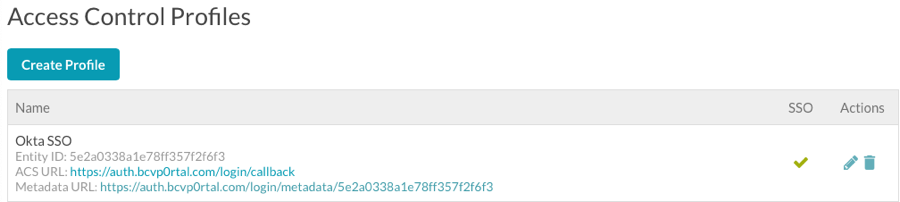
Creating an Access Control Profile
You need to create an Access Control Profile that will be used to secure any experiences you want to secure using SSO.
- Log in to your Brightcove Engage account.
- Click Settings in the header.
- Click Create Profile.
- Give the profile a Name.
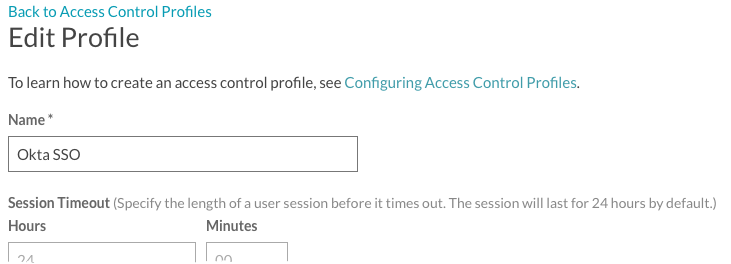
- Return to the How to Configure SAML 2.0 instructions. Copy the Identity Provider Single Sign-On URL and paste it into the SAML 2.0 Endpoint (HTTP) field.
- Return to the How to Configure SAML 2.0 instructions. Copy the entire value in the X.509 Certificate field and paste it into the X.509 Certificate field. Make sure you include the BEGIN/END CERTIFICATE lines.
- Click Save and confirm that the profile was created.
Assigning group permissions
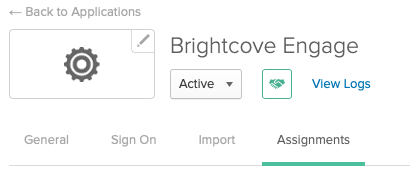
The final step in Okta is to give all users in Okta access to the Brightcove Engage application.
- Return to the Okta Dashboard.
- For the Okta application you created, click the Assignments tab.
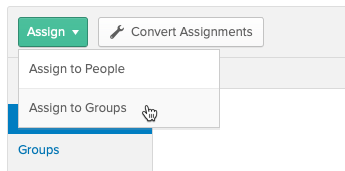
- Click Assign > Assign to Groups.
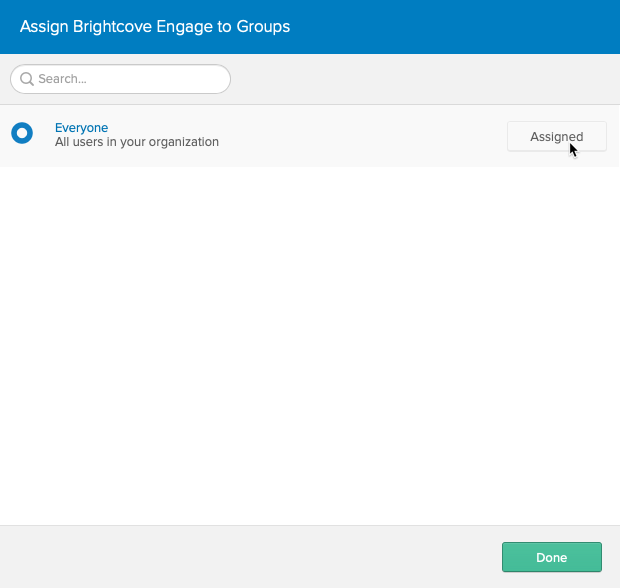
- Click Assign next to the Everyone group and then click Done.
Assign the Access Control Profile to an experience
The last step is to assign the Access Control Profile that was created to the experience(s) you want to secure.
- Return to Brightcove Engage.
- Edit the experience you want to secure.
- In the left navigation, click ACCESS CONTROL.
- Select the Access Control Profile that is associated with the Okta SSO configuration.
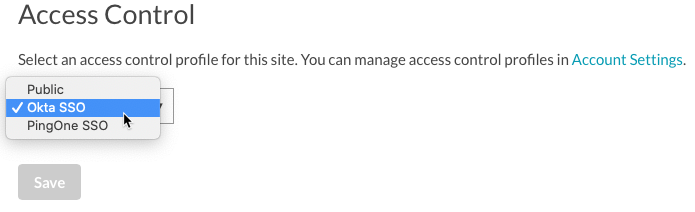
- Click Save.
- Publish the experience.
When you access the experience, you should be prompted by Okta to login. The following image is when trying to access a Mobile App Experience.


